Purple Service description
This document describes the services that Purple provides through the use of its cloud software licensing. The following definitions, service descriptions and information are applicable to the licence and use of Purple’s various products and services.
For the benefit of customers, to offer better services Purple may make changes to their products, platforms and/or services as and when necessary. In all cases, functionality will not thereby be reduced.
Overview of the service
Purple is a cloud-based captive portal solution that allows customers to offer customizable Wi-Fi authentication, collect location data, and analyse, action, report on and/or extract that data.

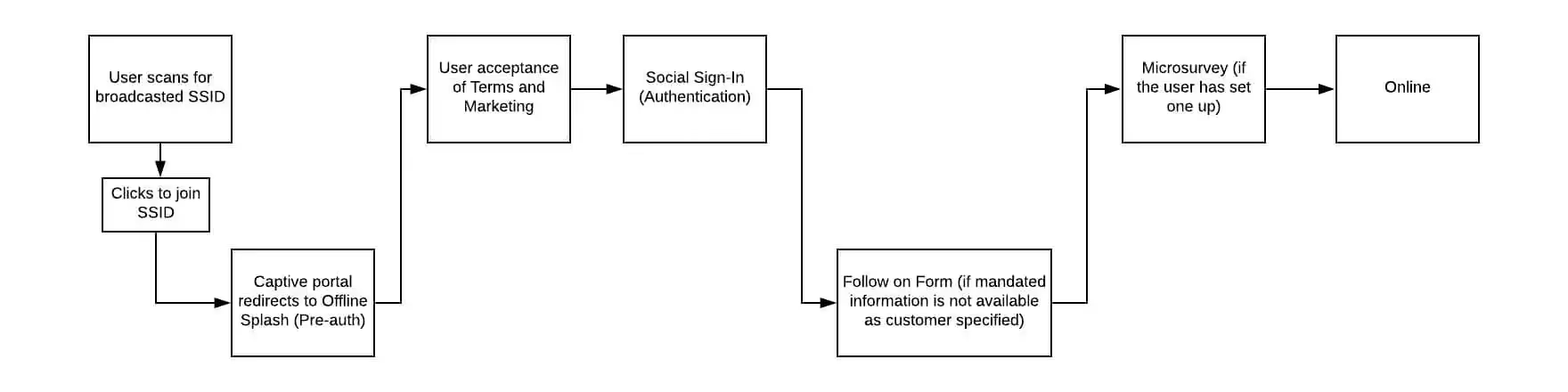
All of the data captured is stored within a centralised reporting dashboard, enabling customers to use to engage more effectively with their guests.
Using the service
The service provides the following functionality. It allows the customer to:
- Set up the guest Wi-Fi access pages and access journey
- Set up the Wireless access points as part of Onboarding a new End User
- Perform admin tasks to set up permissions and roles for a customer’s internal users of Purple’s portal
- View reports, dashboard and provides ability to manage and download them
- Set up marketing emails, sms content, microsurveys and NPS surveys
- Review CRM – a page to find Wi-Fi user contact and visit information
- Set up connectors to combine data with other 3rd party services
- Review license information and status
Guest Wi-Fi
Purple’s Guest Wi-Fi solution is a cloud-based captive portal. When an End User connects to a Wi-Fi SSID and their device makes a request to a domain that isn’t in the configured captive portal list, the request is redirected to Purple’s own cloud-hosted pages to authenticate onto the Wi-Fi. After authenticating, the End User’s device is released from the captive portal and the End User is free to browse the internet.
Supported Access Point/Controllers and configuration
A list of supported network Access Points/Controllers hardware is available in Annex A, with a list of supported firmware versions if applicable, as well as configuration documentation.
Typically, configuration will require defining a splash page pointing at Purple’s cloud hosted splash page, configuring a walled garden list of allowed domains depending on the splash page configuration (see below), and entering Purple’s cloud hosted RADIUS servers for authentication.
Configuration may also require firewall rules to be added so that outbound traffic to UDP ports 1812 and 1813 for RADIUS authentication and accounting traffic. Additionally, UDP port 3799 for Change of Authorisation (CoA) requests to enable a session to be disconnected.
Portal configuration
Within the Purple management portal, a Customer will as a minimum create a Venue, and then within the Venue will enter the MAC address(es) of any Access Point(s)/Controller(s) present at that Venue. These MAC addresses are passed by the Controller to the Splash Page URL, and are used by Purple to determine which splash page to display to the End User.
The Customer can create an Access Journey, which is a collection of configurations (see below for configuration options) that can be assigned to one or more Venues, SSIDs or languages (so it is possible to have different configuration options for different languages selected by the End User – see Annex A for a list of available languages). The Access Journey will also have a specified pre-authentication Splash Page, which is the page delivered to the End User after joining the SSID.
An Access Journey can be applied to a Company, Group, Venue, AP or SSID. These are checked in reverse order – until a matching Access Journey is found (i.e. an Access Journey published to an SSID will take precedence over one assigned to a Company. If a Customer does have multiple Access Journeys, it’s good practice to always have one assigned to the Company without any conditions as a fall-back).
If no Access Journey is created or configured or no matching published Access Journey is found when an End User connects to an SSID, a default Purple-branded Access Journey and Splash Page is delivered to the End User.
Splash Pages
The Customer can configure their own Splash Page, either via Purple’s own drag and drop GUI, or by entering completely custom HTML/CSS/Javascript. These can be created from a blank template, or derived from a number of templates available from Purple. Splash Pages can be either Offline (pre-authentication) Splash Pages that are displayed to an End User when joining the SSID, or post-authentication (Online) Splash Pages that are optionally displayed to the End User after authenticating.
Within a Custom HTML Splash Page, various snippets are available for insertion to allow the Customer to embed dynamic data (such as Venue or Company information, or in the case of post-authentication Splash Pages, End User information such as the End User’s name) or standard elements like authentication links/forms, language selectors or loading spinners.
Following are some of the configuration options available for Access Journeys and Splash Pages.
Authentication methods
Purple supports a number of different authentication methods for End Users to connect via and authenticate themselves, and a Customer can configure one or more from the following list:
Custom Form Fields
A Customer can add up to six custom form fields, which behave exactly as other form fields above. They can be optional or mandatory, and if mandatory, social login End Users will be required to answer them too.
Custom Form Fields can be free of validation, or can be enforced alphanumeric or numeric. Additional advanced validation methods (e.g. for common National ID fields), and with Custom HTML Splash Pages, Customers are free to use whatever front end form validation they wish via JavaScript.
Because Custom Form Fields are created by a Customer and can’t be categorised, any answers provided by End Users are always categorised as personally identifiable information (PII) for the purposes of security, data protection and reporting/analytics.
Seamless Login
The Customer can request that returning End Users (specifically, End User devices recognised by the End User Device MAC that have previously authenticated to the Wi-Fi) are automatically opted back in. This can be at the same Venue, or can be applied across Venues (so that a visitor visiting a second Venue for the first time after visiting another of the Customer’s Venues can log on seamlessly). With seamless login, when the End User joins the SSID, instead of being presented with an offline/pre-authentication Splash Page, they are immediately authenticated with the details they entered previously (after checking that all EULAs associated with the Access Journey have been accepted by the End User).
A repeat End User visiting with a different device will not be recognised for seamless login until they have logged in with that device at least once.
Seamless login can be limited by a seamless timeout, which is defined as a maximum number of days since the last full non-seamless login, or the number of days since the End User last logged in (whether seamlessly or not).
Post-authentication Redirects
Once an End User has authenticated, they can be directed to either a URL entered by the Customer, or directed to a pre-configured Online Splash Page. This redirection is dynamic, and the End User can be shown a different URL/Splash Page depending on the End User’s age, Gender, how many visits they have made to the venue previously, when their last visit was, their platform/browser or whether it’s their birthday).
Most modern Android End User devices (any that use the native Guest Wi-Fi Captive Network Assistant (CNA)) close the CNA as soon as the End User device detects it has been released from the captive portal, so End Users with these devices will not see any configured Post-authentication Redirect.
Marketing Consents
By default, marketing consent is tied to acceptance of the EULA and privacy policy. Within the EU (and optionally outside the EU), a separate marketing consent is required from End Users, via either a separate (default unselected) checkbox or a separate modal with accept or reject buttons (subject to individual assessment based on applicable data protection and electronic marketing laws).
The text of the marketing consent is customisable by the Customer, to cover all of the Customer’s likely marketing use cases.
Custom Terms
Customers can enter their own Terms & Conditions documents, that must be accepted by End Users alongside the default EULA. As well as providing the text of the document, the Customer can provide the document version number. If the version number changes, the End User must re-accept the Terms & Conditions before being allowed to authenticate.
Age restrictions and age-restricted marketing opt-in
The Customer can specify a minimum age for End Users for either Wi-Fi access or marketing opt-in. If an End User is under-age for authentication, they are barred from login. If an End User is under-age for marketing opt-in, they are automatically opted out of any marketing consents.
If an End User enters no age, any restrictions are bypassed – this can be altered by making date of birth a mandatory field in form settings (above).
Email verification
Customers can enable email verification, which will email End Users after authentication to request they click a one-time link to verify their email address.
By default, no action is taken whether an End User verifies their email address or not, but verified email addresses will be marked as verified in the CRM and on exports via API.
Customers can also opt to remove End Users from the Wi-Fi and force them to re-authenticate if they haven’t verified their email address within a configurable amount of time. This disconnection is triggered by a RADIUS Change of Authorisation (CoA) request, sent to the Access Point/Controller from Purple’s cloud hosted RADIUS server (this may require an inbound firewall rule for UDP port 3799 – see the relevant hardware manual in the Hardware list from Annex A).
Most hardware support CoA requests, but some do not – see individual hardware manuals from the Hardware list in Annex A. If CoA is not supported or the Access Point/Controller is misconfigured, the attempt to remove End Users via CoA will fail.
Verify via SMS
If a Customer enables verification via SMS, a one time verification code is sent to the mobile number provided by the End User via SMS. This code is required to authenticate. An End User only needs to verify their mobile number once – subsequent logins will bypass this requirement.
Purple use SMS service providers to deliver this SMS. To enable SMS verification, a Customer must first have an account with an SMS service provider and link their SMS service provider account to Purple in the Purple management portal (at the time of writing, Twilio is the only provider available).
The Customer will be able to choose delivery numbers, manage billing and monitor SMS deliverability, costs and errors via their own SMS service provider account, according to the available functionality of that service provider.
Micro Surveys
Customers may optionally require a Micro Survey to be completed, which is a list of up to five questions that can require a response as a rating (on a scale of 1 to 5), a multichoice answer, or a free text box. This is presented to the End User after authentication but before granting the End User access to the Wi-Fi. Completion of the Micro Survey can be mandatory or optional/skippable.
Micro Survey responses are displayed in the Purple management portal under Campaigns.
NPS Surveys
Net Promoter Score (NPS) surveys can be set up in the Purple management portal by a Customer, for either the entire Company, a single Venue, or any Group of Venues.
NPS surveys work in Purple by sending a templated email to authenticated End Users within 24 hours of an authentication. The email allows the End User to click a rating from 0 to 10 in response to the quest “How likely are you to recommend [venue name] to a friend?”
They will then be taken to a webpage with a secondary question, which will be one of three Customer-configured questions dependent on the score the End User provided – 0-6, 7-8 or 9-10.
The Customer can modify the email by adding a logo.
The NPS score and responses are stored in the Purple management portal under Campaigns. Individual responses are stored and presented in a list that links the response to an individual’s social profile, first name, last name, email address, along with the NPS rating the End User has given.
Logic Flows
Logic Flows are a more visual and granular way of applying configuration, via branching decision trees. They allow certain actions (for example sending of an email/SMS, redirection of a splash page or application of bandwidth restrictions) to be applied according to data collected from the End User’s journey, including but not limited to demographic data (such as age or gender, when available) or the SSID the End User connected to.
MAC Authentication
MAC Authentication is available for most hardware types (see Annex A for a list of hardware manuals, and configuration steps for MAC authentication where available).
If available and configured, once an End User device associates with a network SSID, the Access Point/Controller will first of all attempt to verify the End User device’s MAC address with Purple’s RADIUS servers. If the End User device’s MAC address exists and has a valid session, the End User device is placed online and skips the captive portal process completely, giving a truly seamless Wi-Fi authentication experience.
MAC Authentication can be enabled on a time-limited basis for End User devices that have authenticated to the Wi-Fi, or End User device MACs can be pre-approved (via MAC ‘Whitelisting’ in Venue settings in the Purple management portal). The default time-out period for MAC Authentication is configurable – after this period of time has elapsed, the End User will have to authenticate via the standard captive portal process again.
If MAC Authentication is enabled, any other captive portal steps (such as checking whether the End User has accepted any new EULA, whether the End User has completed all mandatory details, etc) will be bypassed. It is the Customer’s responsibility to ensure that this is compatible with their intended Wi-Fi use case.
SSIDs
To enable a per-SSID Access Journey, Customers can configure a list of SSIDs in the Portal, and apply Access Journeys to these SSIDs. In this way, a single AP can broadcast multiple SSIDs with different experiences (for example, an unrestricted key-protected SSID for staff, and another SSID for guests).
It is important that the SSID names in the Controller/Access Point settings and in the Purple management portal match exactly, and that if an SSID name is changed in one place that it is also changed in the other.
An Access Journey assigned to an SSID takes precedence over an Access Journey assigned to an AP.
Custom User Timeout
Customers can configure a Custom User Timeout in the Purple management portal. If enabled and configured, when an End User authenticates, RADIUS will return the configured timeouts as ‘Session-Timeout’ and ‘Idle-Timeout’ attributes for the End User’s session.
Individual Controllers/Access Points may interpret these attributes differently (see hardware configuration manuals in Annex A), but generally they can be used to override the default session/idle timeouts configured on the Controller/Access Point.
Speed Capping
Customers can configure speed capping separately for upload and/or download speeds, which will apply to all End Users connecting. These are generally applied via RADIUS attributes in the reply from RADIUS when authenticating End User devices. The exact reply/methodology varies according to the Access Point/Controller vendor, and may be limited by the vendor, model or firmware of the hardware.
Where applicable, further details may be available in the applicable hardware manuals.
Tiered Bandwidth
Customers can configure various Guest Wi-Fi payment options through Tiered Bandwidth settings. Default Tiered Bandwidth settings are applied to a Company, and then enabled or disabled at each Venue, with the default options accepted or overruled. In this way, exact pricing, bandwidth, data or speed options can be varied at each venue if necessary. Finally, Tiered Bandwidth settings have to be enabled (or disabled) per AP.
There are three types of Tiered Bandwidth available: session time, speed limiting or data limiting. These are mutually exclusive. It isn’t possible to enable different types of Tiered Bandwidth simultaneously.
Session time allows payment per time period, with configurable scaling costs for different periods of time. It’s also possible to allow End Users a period of free time per time period. The period of time after which available free time resets is also configurable, and a password can be required to activate the free period of time. Session time limits are applied in the same way as Custom User Timeouts (above), with the same caveats.
Speed limiting allows Customers to limit the upload and/or download speed of connected End Users unless they pay for unlimited speed, with configurable scaling costs for different periods of unlimited speed. Speed limits are applied in the same way as Speed-capping (above), with the same caveats.
Data limiting allows Customers to restrict the amount of data an End User can upload/download before being disconnected, with configurable scaling costs for different data size packages. Data use is tracked via RADIUS accounting data, so for data limiting it is essential Purple receive timely RADIUS accounting data (for some Access Point/Controller vendors this may require additional configuration – see hardware manuals linked from Annex A for details per vendor). Once an End User has used more than their data allowance, a RADIUS Change of Authorization (CoA) request is sent to the Access Point/Controller from Purple’s cloud hosted RADIUS server (this may require an inbound firewall rule for UDP port 3799 – see hardware manual) to force the user to be disconnected.
Most hardware support CoA requests, but some do not – see individual hardware manuals. If CoA is not supported or the Access Point/Controller is misconfigured, the attempt to remove End Users via CoA will fail.
Purchased session times are contiguous: if an End User buys 24 hours of time, their purchased time expires 24 hours from the point of purchase, regardless of how much time the End User has spent using the Wi-Fi.
Customers can also optionally generate a list of pre-paid vouchers to distribute to Customers to allow individual End Users to bypass the payment gateway (or for sale offline). These vouchers are available for all Tiered Bandwidth types.
When an End User attempts to authenticate to a network with Tiered Bandwidth configured and active, after authenticating themselves they are presented with the available purchase options and can choose a purchase option to proceed to payment, or if an existing paid session is identified (linked to the End User account) their paid session is resumed.
End User payments are taken using a third party payment gateway (currently Stripe – additional or replacement payment gateways maybe available in future). Purple store no End User payment information other than a transaction ID.
In all cases, when an End User’s session is ended, the captive portal process will begin again, allowing them to purchase again.
Because a Wi-Fi session can’t be interrupted by the End User, once an End User has purchased a tier (or begun a free session), they are unable to change their session until the current session has ended (e.g. to upgrade their speed settings or extend their session).
Supported End User devices/browsers
Purple aim to provide Guest Wi-Fi onboarding support for modern versions of the most popular browser/operating systems, which means at least the default configurations of End User devices that are 3-4 years old. Although it’s impossible to test every combination of settings with every version of every platform available, Purple do extensive QA testing with many different hardware and software combinations. Purple recommends that Customers check their proposed combinations in advance of any implementations.
Purple test the various Captive Network Assistants (mini-browsers that mobile phones and tablets use to authenticate to Wi-Fi captive portals) native to each Android and iOS version. An exact matrix of officially supported browsers and operating systems can be found in Annex A.
Because Customers can create their own bespoke Splash Pages, Customers take responsibility for cross-browser testing their own Splash Pages. Any third party script/asset sources will need to be allowed within the captive portal (by including the domain names of those sources and any dependencies those sources may have), but Customers should also be aware that changing the recommended list of allowed captive portal domains may also impact the End User experience, especially with regard to the way Captive Network Assistants detect whether the End User device is within a captive portal. More information on this can be requested from Purple’s support team.
Analytics
The reporting capabilities in Analytics can be accessed at different levels of hierarchy: Customer, Group and Venue. The number of reports and functionality available will depend on the licenses the customer has and what permissions the individual user has.
Reports
Behaviours
Reports in the Behaviours suite provide analytics based on end Wi-Fi user behaviour allowing Purple’s Customers to understand intent and predict future actions.
– Frequency* – This report counts the number of visitors seen making 1, 2, 3, 4 or 5+ visits over a period of time. Visitors are moved along the groupings based on the number of visits they have made in total. The groupings are based on the count of visits and a visitor will only ever be counted in one of them.
– Bounce* – This report provides an insight into the number of stayed and bounced visits at Customer’s venues. Bounce is based on the duration a visitor’s device was present within range of a hardware controller in your venue during their visit. Visits are categorised as ‘Stayed’, ‘Bounced’ or ‘Unknown’.
– New vs Repeat – This report shows the number of new and returning visitors within a given date period.
– Engagement* – This report provides an insight into end Wi-Fi user engagement at the customer’s venues. Engagement is based on the duration a visitor’s device was present within range of a hardware controller in the venue during their visit. Visits are categorised as ‘Not Engaged’, ‘Partially Engaged’, ‘Fully Engaged’ or ‘Unknown’.
– Dwell* – This report provides an insight into the average amount of time visitors spend within the customer’s venues on. Dwell is based upon the average duration a visitor’s device was present within range of a hardware controller in the venue during their visit. If no valid duration is found for a visit then it is not included in the average.
– Hour of Day* – This report provides an insight into the average number of visits to the customer’s venues by hour of day. Hour of day is based upon the hour a visitor’s device entered the range of a hardware controller in the venue and the duration it remained connected. Visits are counted once in the hour which they connected and again in every hour or part thereof which they were within range of a hardware controller and remained connected.
– Day of Week* – This report shows the average number of visits made to the customer’s venues by day of week e.g. (Monday, Tuesday, Wednesday, etc). Visitors are counted once per day in the current scope, but can be counted multiple times within the date period used in the report.
Network Usage
– Overall Usage – This report shows the amount of data uploaded and downloaded by the customer’s visitors within a given date period.
Technology
– Connection method* – This report provides analysis on the connection methods that visitors used when they connected to the Wi-Fi within a given date period. The connection method may be a non-social method (e.g. registration form) or a social network method (e.g. Facebook, Twitter etc).
– Device type – This report shows the device type (e.g. mobile, desktop or tablet) that visitors used when they accessed the Wi-Fi network within a given date period.
–
– Browser – This report shows the internet browser (e.g. Edge, Chrome, Safari etc) that visitors have used to access the Wi-Fi network within a given date period.
– Platform – This report shows the platform (e.g. Android, iOS etc) that users were using when they connected to the Wi-Fi network within a given date period.
– Operating system – This report shows the operating system (e.g. Windows, Mac OS, Android etc) that users were using within a given date period.
Users
– Location* – This report shows the top 15 most reported visitor ‘home towns’ within a given date period.
– User count* – This report shows the number of distinct audience members who have visited the current scope within the date period specified. Audience members will be counted once per day, with their earliest visit recorded if viewed hourly.
– Gender* – This report shows the gender breakdown of distinct audience members who have visited the current scope within the date period specified. Audience members will be counted once per day, with their earliest visit recorded if viewed hourly.
– Age* – This report shows the age breakdown of distinct audience members who have visited the current scope within the date period specified. Audience members will be counted once per day, with their earliest visit recorded if viewed hourly.
– Language* – This report shows the first language of distinct audience members who have visited the current scope within the date period specified. Audience members will be counted once per day, with their earliest visit recorded if viewed hourly.
Visits
– Visit count* – This report shows the number of visits to the to the current scope within the date period specified. Audience members may be counted more than once per day.
– Age* – This report shows the age breakdown of visitors to the to the current scope within the date period specified. Audience members may be counted more than once per day.
– Gender* – This report shows the gender breakdown of visitors seen in the current scope within the date period specified. Audience members may be counted more than once per day.
– Cumulative* – ‘Cumulative’ will show the user:
- A cumulative total of the number of ‘visitors’ visiting the current scope grouped by time
- A cumulative total of the number of ‘visits’ at the current scope grouped by time
The user will be able to see the accumulated values over time for each grouping, ‘visitors’ and ‘visits’.
Analytics Filters
The below are current list of filters available. However, Purple reserves the right to add or remove filters as needed to continue to deliver an enhanced experience to the end user in order to keep up to date with industry and technology.
Date picker / calendar
Controls the selection of custom or pre-defined date ranges including:
– Last 7 days
– Last 30 days
– Last 6 months
– Last 12 months
– All time
Analytics (General functions)
– Scope by Hour, Day, Week, Month, Year, Categories
– Chart types: Bar, Column, Line, Scatter, Spline, Area, Pie
– Data grouping by: Stacked, Split, Percentage
– Stack filters, Segment filters
– Authenticated/ Unauthenticated data (P)
– Data table
– Dimension selector*
– Download as PDF or CSV
– Schedule Reports
– Custom Dashboards
*Available with the Enterprise License only
(P)Requires Presence License
Additional reporting
Campaign reports
– Marketing
These reports provide the customer with analytics for Splash page and Eshot marketing campaigns. The reports provide an insight into the number of campaign views and provide totals segmented by visitor demographics (e.g. gender, age range) where demographic data can be obtained.
– Micro Survey
These reports provide the customer with micro survey response data that has been collected from visitors who were presented with and opted to provide a response to a micro survey when they authenticated on to the Wi-Fi network.
– NPS Survey
These reports provide the customer with NPS response data where a NPS survey was emailed to a visitor and the visitor opted to provide a response. The reports provide the customer with an overall NPS score based on feedback from their visitors.
Presence – Overview reports
– Bounce rate (P)
This report shows the customer the number of end user devices that were seen on the Wi-Fi network and categorised as ‘Bounced’ or ‘Stayed’ within a given time period. ‘Bounce’ is calculated from visit duration where devices with a duration less than 3 minutes are categorised as ‘Bounced’. Customers are able to configure their own value for ‘Bounce’ in order to customise the threshold that is used.
– Conversion (P)
This report shows the number of devices that were seen on the Wi-Fi network and categorised as ‘Converted’ or ‘Passed’ within a given time period. ‘Conversion’ is calculated from RSSI and where visits fall beneath a particular RSSI strength then they are categorised as ‘Passed’.
– Repeat vs. new (P)
This report shows the number of ‘New’ and ‘Repeat’ devices that were seen on the Wi-Fi network within a given time period.
– Duration (P)
This report shows the average daily visit duration in minutes for a given time period.
– Time of day (P)
This report shows the number of devices seen within each hour of the day within a given time period. The totals for each hour are based on the time / hour that each device was first seen on the network within the reporting time period.
– Visitors per day (P)
This report shows the total number of unique devices seen by day for the reporting period selected by the customer.
– Visitor engagement (P)
This report shows the number of devices that were seen as ‘Not Engaged’, ‘Partially Engaged’ or ‘Fully Engaged’ within a given time period. ‘Engagement’ is based on end visitor device visit duration. The thresholds for each category can be configured by the customer.
Venue level reporting
The reports available at Venue Level will be accessible to anyone with Customer Level access or to users that have been granted permission to view that particular venue or group of venues. As Venue Level Reports are more granular, certain reports are only available with Location Licenses from now referenced as (L) or Purple Protect Licenses referenced as (PP). Note the reference to the licenses are based on currently existing license types. These license types may be changed or removed by Purple and new types created.
Network reports
– Top requested domains (PP)
This report shows the top domains (e.g. google.com) that were requested by the customer’s visitors when they were connected to the Wi-Fi network.
– Top requested categories (PP)
This report shows the top domains by category (e.g. Sport, TV, Shopping etc) that were requested by the customer’s visitors when they were connected to the Wi-Fi network.
– Most blocked domains (PP)
This report shows the most common domains where network requests were blocked by content filtering.
– Most blocked categories (PP)
This report shows the most common domain categories where network requests were blocked by content filtering.
Location – Floorplan management
– Overview reports (L)
This report displays visit counts for floorplan zones showing the total number of devices seen in a zone over a 24-hour time period. The customer is able to select the 24-hour period that they wish to report on and the report will display both the device current for the current second of the day and the device count for the 24-hour period for each zone. The report also provides the customer with device counts segmented by visitor demographics including gender, connection method and age.
– Data overlay
This feature within Floorplan Management analytics allows the customer to see their footfall by age range, connection method and dwell time. Individual devices are highlighted on the venue floor plan depending on which segment the customer has chosen to view.
– Visitors and devices
This report displays a list of known and unknown visitors for devices seen in a given second within a 24-hour time period. The customer is able to select the 24-hour period that they wish to report on and is able to use timeline controls in the Floorplan Management user interface to determine the second of the day that they wish to see the list for.
– Heatmap / footfalls view (L)
The Floorplan Management feature provides the customer with both a raw footfall view of visitor devices within their venue and a heatmap view over a 24-hour time period. The customer is able to toggle between heatmap and footfall view with the heatmap view allowing the customer to see ‘hotspots’ within their venue for any given second of the 24-hour time period. The customer is able to select the 24-hour period that they wish to report on and is able to use timeline controls in the Floorplan Management user interface to determine the second of the day that they wish to see the footfall for.
Location – Zone analytics
– Visitor journeys (L)
This report shows visitor journeys through the venue showing the number of devices seen moving from zone to zone within the venue. The report includes counts for through traffic and drop off for each zone also providing the customer with gender counts for each zone where demographic data can be obtained. The customer is able to view journey data for the last 7, 14- and 30-day periods from the current date and the customer is able to further filter visitors by gender and age range. The report provides the user with 2 visualisations of the data, the ‘journeys’ view and a ‘pathing’ view. The ‘journeys’ view provides the customer with a flow diagram of the data and the ‘pathing’ view provides a sunburst chart view.
– Average dwell for zones (Top 10) (L)
This report shows the average dwell for the venue’s floor plan zones. The average dwell is computed from device visit time with the report showing the Top 10 zones with the highest average dwell time for the reporting period that has been selected.
– Average visits for zones (Top 10) (L)
This report shows the average number of visits displaying the Top 10 zones with the highest number of visits. Counts are based on counting devices once where they are seen in each zone for the reporting period that has been selected.
– Heatmap of people by hour (L)
This report provides the user with a heatmap view of zone visits for each hour of the day. The report shows the heatmap chronologically for the reporting period that has been selected where the customer is able to see both the heat and the number of visitors seen in each zone for each hour of each day within the reporting period.
Marketing
Communications
Customers can send emails (‘Eshots’) or SMS to their Customers via the Purple management portal. This communication can be a single email template sent to all or a segment of End Users who’ve authenticated to the guest Wi-Fi, as an ongoing campaign triggered by events, or both.
A communication can be one of six types:
Visit-based, dwell and top Customers communications can be further segmented by age, gender, the number of visits the End User has made, or whether the End User visited in a given date range. For the purposes of these filters, a ‘visit’ is defined as a date an End User logged in at a Venue one or more times (e.g. 5 logins across 3 days would be 3 visits).
Ongoing communications triggered by an End User logging in or dwelling in a zone will be close to real-time, but may lag behind the actual event by a minute or two.
Eshots
Customers can build emails using Purple’s simple drag and drop GUI, using 5 basic elements: a title, a text box, an image, a ribbon and a date range.
In general, emails are dispatched within a minute of being published/triggered, but larger email sends may take longer before they are fully dispatched.
Purple do everything possible to ensure email deliverability, including building domain trust by monitoring hard and soft bounces to permanently blacklist undeliverable email addresses to minimise bounce rate, following email best practices such as having a single-click opt-out for all marketing communications, ensuring Purple emails go from IP addresses used exclusively for Purple emails, and having appropriate email domain configuration. However, some emails may be identified as spam.
In some cases emails may be sent from a Customer’s own email address, from a Customer’s own domain. In these cases, the Customer has responsibility for ensuring the configuration and domain trust are maintained properly to ensure the best possible deliverability of emails.
Emails are subject to a fair usage policy of a maximum of 4 email sends per End User who has authenticated to your Wi-Fi per month.
Campaigns
Emails may be converted to a campaign, which allows the insertion of a link. When this happens, every element within an email becomes a link. Clickthrough metrics for links are provided in the Campaigns section of the Purple management portal.
SMS
SMS are text-only, and delivered by SMS service provider using the Customer’s own account. Before sending SMS messages, a Customer must have a valid SMS service provider account and link it to the Purple management portal, as detailed above under ‘Verify with SMS’.
Some countries have different rules for marketing SMS communications and one-time password communications. The Customer should be aware of and comply with the applicable regulations of the countries they’re sending SMS to, and may need to go through additional checks with the SMS service provider before being allowed to send SMS messages within some countries.
CRM
The CRM lists the details of all End Users who’ve logged in at a given Company or Venue(s). Every End User or End User device that has authenticated under the currently selected Company, Venue or Group of Venues is represented as a distinct card, which contains most information known about that individual End User or End User device.
The CRM has an index page that allows the Customer to filter the cards by either system tags (such as card type, age, gender or authentication method) or by user-defined tags. The index page also has a search box that allows a Customer to search for cards by name, email address or MAC address.
The individual cards display different data depending on whether the card type is an End User or End User device, but contain profile information such as name, MAC address, date of birth or marketing opt-in status, as well as a list of authentication’s, communications sent, associated End User devices/End Users, social information if applicable, and paid session information.
Both the index and individual cards are downloadable in CSV format.
Data export
There are multiple ways for Customers to extract data from the Purple platform to transfer to other platforms/data stores.
It is the Customer’s responsibility (to ensure that the exported data is stored and handled in a way compatible with the applicable data laws and regulations.
APIs
Purple have a RESTful Customer API that allows export of most End User data. Access is strictly via TLS, and signed via public and private key with a date/time to help prevent interception and replay attacks.
Keys and full documentation can be requested from the support team.
Webhooks
Webhooks are outbound data pushes, triggered by events such as an End User authenticating to the Wi-Fi.
A Customer can enter a URL (must be HTTPS) and, once verified, any End User logins will be pushed to that URL in a defined JSON format. The data is a subset of the complete End User data including the most commonly used data (such as email address, name and date of birth) and includes all the information required to make a follow-up request to the RESTful Customer API (above) to recover further information.
Connectors
Connectors are easy-to-use methods of exporting data to common third party services, including CRM systems like Microsoft Dynamics or eCRM platforms like Mailchimp. As with Webhooks (above), data is pushed to these services whenever an End User authenticates.
Custom data exports
Purple can also export data to many other proprietary systems. These integrations are charged as professional services, and assessed on a case by case basis. Customers can contact their Purple account manager to request custom data export feeds.
Profile portal
After authentication, End Users will be sent a link to a portal where they can view data held about themselves, view (and change) any opt-in consents and immediately delete all data collected about themselves.
The Customer has no access to this portal.
Location data
Location data is data collected passively by compatible APs when End User devices (both authenticated and non-authenticated) probe for Wi-Fi SSIDS, or engage in traffic on the network. Typically, an AP records a received signal strength indication (RSSI) value, a MAC address (which may be randomised, depending on the End User device operating system) and a date/time for each End User device Wi-Fi probe/traffic event. With the right hardware and multiple APs, this data may be enhanced to an estimated geometric coordinate of the End User device relative to the uploaded floor-plan.
Location data needs the correct license add-ons to unlock (see Licenses).
Presence reports deal only with the RSSI value and event times, looking at visit analytics for a Venue as a whole (see Analytics for descriptions of individual presence reports). These are especially useful where a vendor doesn’t provide coordinate data or a Venue doesn’t have sufficient AP coverage to generate accurate coordinate data.
Individual End User device events are aggregated into visits by joining data points no more than 90 minutes apart to create a start and end date for a visit and the minimum and maximum observed signal strength for each visit.
Location reports deal with geometric coordinate data, allowing reporting on the reported positions of End User devices within a Venue, the drawing of geometric zones to track paths taken through a Venue, and heatmaps.
Location reports focus on a floor plan/map of a Venue that is uploaded to the Purple management portal via our support team. Once uploaded, a Customer will be able to draw geometric zones on the floor plan. Once data is available, a Customer will be able to select dates and times on the floor plan to see visitors present within those time periods at both a Venue and zone level, and see heatmaps of visitor activity (see Analytics for descriptions of location and zone reports).
When an End User device MAC is recognised as having logged in via Purple in the past, some demographic data may be associated with the location data records (gender, age). Where an End User has logged into this venue before and accepted the venue’s T&Cs, a recognised End User device will be linked against the End User record, regardless of whether the End User is currently authenticated to the Wi-Fi.
Purple can identify and filter out randomised MAC addresses (End User devices like modern iPhones that do not present their true MAC addresses until authenticated to the Wi-Fi), and anonymous MAC addresses (addresses that haven’t authenticated to the Wi-Fi) are hashed with a company-specific key on export via API to prevent sharing of data about anonymous End User devices and comparisons with third party data sources.
The quality of location data differs hugely depending on many factors. Guides are available on optimising Access Point layout for the most accurate location data, but some Venues may have architectural features that inhibit the collection of accurate data.
Presence and location data are excellent ways of seeing footfall patterns, but cannot give accurate footfall counts.
Purple keep aggregated location data indefinitely (start and end times of visits to Venues/zones, maximum/minimum signal strengths recorded) but only commit to keeping individual probe packets for 24 hours because of the volume of data.
See the hardware manuals linked from Annex A to see which APs support the collection of location data. Some vendors require additional hardware and/or licenses to collect location data.
Content filtering
Customers can enable content filtering after purchasing additional per-AP licenses.
Content filtering is DNS-based – the Customer updates their Controller configuration to point at Purple’s DNS servers (a service provided by a third party DNS provider, Web Titan). Restricted domain names resolve to an IP hosting a page informing the End User that the content they were trying to reach is restricted.
Content filtering can be enabled by categories which include constantly updated lists of relevant domain names, and Customers can also add their own restricted domain names via the Purple management portal.
If content filtering is enabled, new reports are enabled showing most commonly resolved domain names and domain categories, as well as the most blocked domain names and categories. These reports are associated with a Venue by IP address (using the Venue’s WAN IP address), to give Customers an approximation of what sites End Users are visiting while using the Wi-Fi. If multiple Venues share an external IP address (e.g. sharing a common gateway to the Internet), the domain reports for those Venues will be merged.
This data can’t be associated with individual End Users.
Security and data protection
Data in transit
All public facing portals and websites are encrypted with TLS (Transport Layer Security). TLS is the standard security technology for establishing an encrypted link between a web server and a browser. This link ensures that all data passed between the web server and browsers remain private and integral. Purple support TLS versions for their lifetimes, and remove access to TLS versions that expire (e.g. TLS1.0 in 2018 and TLS1.1 in March 2020).
Purple regularly review TLS ciphers offered, and remove ciphers that are no longer considered to meet minimum security requirements.
Data at rest
All data is hosted within Google Cloud (GCP) or Amazon Web Services (AWS), and all disks hosting data are encrypted (AES-256).
All passwords are encrypted with the bcrypt hashing function.
Data protection
Purple’s system allows for data to be hosted and handled in a way consistent with the standards of the EU’s GDPR regulations and other applicable regimes.
All data purposes and rights may be explained clearly and transparently to the End User in Purple’s EULA and privacy policy, which may be presented in concise and user-friendly terms.
Separate active opt-in may be sought for all marketing consents, and any EULA or opt-in consent is stored against the End User and Venue with the date, time and language of opt-in. Once an End User has logged in, they are sent a link to an End User profile (Profile Portal, see above) where they can view data held about themselves, view (and change) any opt-in consents and immediately delete all data collected about themselves.
Additionally, End Users can directly email a Data Protection Officer (via a clearly displayed email address) with any queries, for any changes to their data or to exercise their right to be forgotten.
Data is only used by Purple for the agreed and stated purposes, (although the individual Customers decide their own data uses and configure the portal to collect the information required by themselves, as well as uploading their own additional EULAs and privacy policies where required, consent of which is tracked individually).
Purple have a declared data retention period of 13 months of inactivity, after which all PII data about aa End User are destroyed. Purple retain only strictly anonymous data for reporting purposes.
Security
Purple are ISO-27001 certified, and have a comprehensive internal Information Security Policy covering all aspects of data storage and handling. Purple’s policy covers physical security, disaster recovery, incident reporting and management, access privileges, media destruction, server and network hardening, change control management, secure software development, and more.
Hosting and service availability
Hosting
Purple currently host all services on Amazon Web Services (AWS) and Google Cloud Platform (GCP). Purple maintain and deploy infrastructure as code, with templates to create identical regions/zones around the world. In this way, Purple can utilise different cloud environments.
Both AWS and GCP have well documented and publicly available security accreditations.
Scaling and availability
Purple’s services are built to scale horizontally in the cloud, allowing the solution to scale to meet traffic demands. We monitor our infrastructure and adjust our capacity accordingly intended to maintain steady performance across our servers by splitting services across availability zones with the intention of minimising single points of failure. Purple’s public endpoints are also backed by GLB or ELB which distribute load between multiple servers, allowing us to scale both vertically & horizontally in case of a traffic surge.
Purple’s SLAs are monitored through simulated Wi-Fi logins.
Monitoring
Purple have automated monitoring performance metrics with SLAs for response times to incidents.
Deployment model
Purple’s software is made available via Purple’s cloud, and all software updates are automatically applied to all Customers on deployment. There can be a period of time between the first Customer receiving the update and the last as the deployment roles out internationally. Small updates and bug fixes are deployed constantly, and a weekly change list is available on the Purple management portal. Because all customers are using the latest version of the software, it isn’t possible for an individual customer to roll back to a previous version.
Larger updates (updates that significantly change the Customer experience) are publicized in advance where possible, and may include preview videos or training seminars.
Occasionally, these larger updates will be available to Customers via a beta platform where the Customer can switch to preview the beta platform and then back to the current, stable platform.
Offboarding
Data extraction at end-of-contract
The Customer can at any time extract all data via Purple’s existing APIs, documented above under Data Export.
End-of-contract processes
Can be agreed on a case by case basis.
Licensing
Purple operate a Software as a Service (SAAS) software licensing and delivery model. See individual contract terms for details.
Unless otherwise agreed, all licenses activate on the purchase date and expire from the activation date, regardless of whether they’re currently assigned to an AP.
Support and training
See separate contract documents
Feedback
The future development and direction of the Purple Platform is driven by our customers. We use Receptive as a channel for our partners and customers to share their user stories, pain points and feedback and enable them to raise feature requests. All requests are reviewed and we currently action approximately 20% of these. Typically, a request is acknowledged within 24 hours of being received. It is then reviewed for market demand and product fit. Successful requests are then brought to a bi-weekly meeting consisting of senior product stakeholders within the business. If the request is successful and aligns to our roadmap it will go into our development backlog to be picked up by one of our development teams in the future. All status changes of the request are communicated out via email and within the Receptive platform.
ANNEX A
Data collected by authentication method
Supported Wi-Fi Hardware
Supported Web Browsers
Supported Languages
We have translated our platform into 40+ languages. We have the ability to translate content in our access (onboarding) journey separately to the content in the Purple Portal.
Users are automatically presented with the language matching their browser’s configuration (if available), otherwise the platform falls back to English. Users can use a simple drop down to change their language at any point should they wish to.
Annex B – Table of acronyms / definitions
Venue
A venue is a unique location for a customer which will host the wireless access point hardware to facilitate guests connecting to a Wi-Fi network
Customer
A customer is the company who has purchased licenses to use one or more Purple’s services.
Access Journey
A collection of configuration (see below for configuration options) that can be assigned to one or more Venues, SSIDs or languages and is associated with a Splash Page; or the journey a user takes to onboard to the Wi-Fi
AP
Access Point
API
The programming interface that allows (in Purple’s case) Customers to extract data from the Purple platform
Captive Network Assistant
The Captive Network Assistant (CNA) is the mini-browser that a phone, tablet or PC may launch when a user joins a Guest Wi-Fi network with a Captive Portal. Typically, the End User Device will attempt to reach a pre-configured URL that it knows it should be able to reach if it has unrestricted Wi-Fi – if that request is redirected, the device assumes a Captive Portal and launches the Captive Network Assistant to allow the End User to authenticate.
The CNA is specific to the Operating System running on the End User device, and will differ from platform to platform (or not be present at all).
Captive Portal
The Captive Portal (or Walled Garden) refers to the limited Internet access granted to a Guest Wi-Fi device after joining a Guest Wi-Fi network but before authentication. A Guest Wi-Fi device will have access to a limited list of domain names, and any requests to domains outside of this list will be redirected to the Offline Splash Page, prompting the user to authenticate.
Note: attempting to redirect https URLs will cause a TLS certificate error to be displayed to the End User, warning them that their secure connection is being hijacked/redirected. This is one of the reasons for the existence of the Captive Network Assistant (above).
Connectors
Purple allows the association of 3rd party data from external systems with its own Purple Portal. This data is coupled with the portal using pre-built ‘Connectors’.
CSV
A text file format separated into columns (separated by commas) and rows (separated by new lines).
Customer Level Reports
A suite of reports aggregating data across the customer’s entire estate.
Eshot
A short marketing-focused email that can be branded and customised, and then delivered to a target audience by demographic, visit, location or dwell.
End user
Refers to the user of the Guest Wi-Fi network, sometimes referred to as the ‘Guest’ or ‘User’.
Group level reports
A suite of reports aggregating data across a group of venues. Customers have the ability to create and manage their own groups form within the Purple Platform.
Guest Wi-Fi
Guest Wi-Fi describes the service where people may obtain Internet access, typically using Wi-Fi technology, via a wireless local area network (WLAN) using a router connected to an internet service provider, and typically via a captive portal.
Onboarding
Onboarding refers to the process of authenticating an end-user onto the Wi-Fi network, and any additional actions that may be associated to that experience.
Offline splash page
The offline splash page is the default first stage of Purple’s access journey. Presented on a device once end-users have connected to the guest Wi-Fi SSID, it provides access to the guest Wi-Fi network. End-users are contained within a walled-garden and are not online at this stage.
Online splash page
The final stage of the access journey. The online splash page is a customisable landing page notifying end-users that they are now online.
PDF
A file format used to present documents. Reports downloaded within the Purple Portal can be downloaded in PDF format.
Purple portal/Purple management portal
Purple’s platform for the management of the Guest Wi-Fi network, venue, groups and estate and all available Purple features
Seamless authentication
As part of Purple’s Access Journey, the customer can choose to re-authenticate repeat visitors seamlessly on to this Wi-Fi network. In this case repeat users will not need to enter their login details upon a repeat visit but instead will be recognised and forwarded directly to the online splash page or URL redirect.
Splash page
A Splash Page is a customisable page displayed to the End User as part of the Guest Wi-Fi onboarding journey.
SSID
Service Set Identifier is the name given to a broadcasting Wi-Fi network which is used by Wi-Fi users to connect to the network they intend to use to get online. This can be explicitly communicated to the users by advertising or named in line with the venue or business. This is at the customer’s discretion and choice and Purple has no control over this chosen name.
Venue level reports
A suite of reports offering detailed insights specific to each particular Venue within a customer’s estate.
Walled Garden
See: Captive Portal






