A Practical Guide to Security in Networking
When we talk about true network security, it all boils down to three core ideas, a model known in the industry as the CIA Triad: Confidentiality, Integrity, and Availability. This isn't just theory; it's a practical framework that helps balance the critical need to protect data with the equally critical need for it to be accurate and accessible. If even one of these pillars wobbles, the entire security structure is at risk.
Understanding the Foundations of Network Security

To build a defence that can actually withstand an attack, you first have to get a handle on the principles that define a secure network. Before diving into complex tools and strategies, grasping what is cybersecurity at a fundamental level is the essential first step. These principles, the CIA Triad, are the bedrock for every single security measure you'll ever put in place.
Think of it like a secure courier service tasked with delivering a critical business contract. Every part of the triad plays a distinct and vital role. Get one part wrong, and the whole delivery becomes untrustworthy.
Confidentiality: Keeping Secrets Safe
Confidentiality is all about making sure data is only seen by the people who are supposed to see it. In our courier analogy, this is the sealed, opaque envelope that stops anyone but the intended recipient from reading the contract inside.
In the world of networking, we achieve this primarily through encryption. When your data zips across a network, encryption scrambles it into a completely unreadable format. Anyone who manages to intercept it without the right decryption key just sees a meaningless jumble of characters. This is what protects sensitive info like passwords, credit card numbers, and personal data from prying eyes.
Integrity: Ensuring Data Is Unchanged
Integrity is the guarantee that the information you receive is the same information that was sent, with no sneaky alterations along the way. For our courier, this is the tamper-evident seal on the envelope. If that seal is broken, the recipient immediately knows the contents might have been messed with and can't be trusted.
This principle is absolutely crucial for maintaining the reliability of your data. Network security measures like cryptographic hashes and digital signatures act as this digital seal, verifying that the data has arrived exactly as it was sent. This stops attackers from doing things like changing payment amounts or modifying commands sent to critical systems. For a deeper dive, our own data and security overview explores these processes in more detail.
The CIA Triad isn't just a textbook model; it's a practical framework for assessing risk. Every security decision—from picking an encryption standard to setting up a firewall rule—should be weighed against its impact on confidentiality, integrity, and availability.
Availability: Ready When You Need It
Finally, availability is the promise that authorised users can get to the network and its resources whenever they need to. The courier service is useless if it can't deliver the package on time. If it's always late or the van breaks down, the service fails.
In networking, threats like Denial-of-Service (DoS) attacks are designed to smash this pillar. They do it by flooding a system with so much junk traffic that it gets overwhelmed and can't respond to legitimate users. Building robust network security means creating resilient systems with backups, redundancy, and proactive monitoring to ensure services stay online and working, even when under attack.
Common Network Threats Every IT Administrator Should Know
Understanding security theory is one thing, but knowing what you’re up against in the real world is another. The threats facing your network aren’t just abstract concepts; they are active, evolving tactics used by attackers to disrupt your services, steal sensitive data, and compromise your entire organisation.
For businesses in hospitality, retail, or healthcare, the risks are magnified. When you’ve got public-facing WiFi operating alongside systems handling sensitive internal data, a breach can be catastrophic, leading to huge financial losses and shattering customer trust.
Let's break down some of the most common attacks you need to be watching for.
Man-in-the-Middle Attacks
Imagine two people passing notes in private. Now, picture someone sitting between them, secretly intercepting every note. They can read it, change it, and then pass it along without either person knowing they were ever there. That’s the essence of a Man-in-the-Middle (MITM) attack.
In a network setting, an attacker places themselves between a user and a legitimate service—say, a guest connecting to your hotel's WiFi. From that position, they can eavesdrop on all communication, capturing everything from login credentials to payment details. This is especially dangerous on unsecured or poorly configured public WiFi networks, where users are most vulnerable.
Rogue Access Points
A Rogue Access Point (AP) is a malicious wireless hotspot set up to impersonate a legitimate one. Think of it as a fake shopfront designed to look exactly like a real, trusted brand. A hotel guest might see two WiFi networks: "GrandHotel_GuestWiFi" and "GrandHotel_Guest_WiFi". One is real; the other is a trap set by an attacker.
If the guest connects to the rogue AP, the attacker gains complete control over their traffic. They can launch MITM attacks, redirect the user to phishing sites to steal credentials, or even inject malware onto their device. It's a simple but alarmingly effective tactic that preys on unsuspecting users.
A secure network should never be a guessing game for the user. Technologies that automate secure connections, like OpenRoaming, eliminate the risk of a user accidentally choosing a malicious network, as the device connects automatically and securely without any user action required.
The scale of these vulnerabilities is massive. UK cybercrime statistics highlight the financial impact, with reports of cyber-enabled crimes resulting in £1.63 billion in financial losses. For businesses in sectors like information and communications, 43% experienced breaches. These disruptions included temporary loss of network access for 7% and website downtime for 6%. These aren't just numbers; they represent real-world consequences of attacks like Denial-of-Service. You can read more about the latest UK cyber crime trends and see how these threats are impacting businesses today.
Lateral Movement and Its Dangers
Once an attacker gets a foothold in your network—maybe by tricking one user with a rogue AP—their work has only just begun. The initial breach is rarely the end goal. Instead, they start a process called Lateral Movement.
This is the digital equivalent of a burglar getting through one unlocked window and then quietly moving from room to room, looking for the safe. The attacker explores the network internally, seeking out more valuable targets like servers with customer data, payment systems, or administrative accounts. This stealthy navigation is how a minor breach escalates into a full-blown catastrophe.
Denial-of-Service Attacks
A Denial-of-Service (DoS) attack has a much more direct, disruptive goal: to make your network or service completely unavailable. Imagine a single entrance to a busy shop being completely blocked by a crowd, preventing any actual customers from getting inside. That's a DoS attack.
In the WiFi world, a common variant is a deauthentication attack. The attacker floods the network with forged commands that forcibly disconnect everyone from the WiFi, effectively shutting it down. For a hotel, shop, or event venue, this can bring operations to a grinding halt, stopping point-of-sale transactions, guest services, and internal communications in their tracks. This directly compromises availability—the third pillar of the CIA triad—and causes immediate financial and operational damage.
To help put these concepts into context, here’s a quick rundown of common threats and how they can impact a business, especially one offering public-facing WiFi.
Common Network Threats and Their Impact
As you can see, the methods vary, but the end goal is always to exploit a vulnerability for an attacker's gain. Knowing what to look for is the first critical step in building a resilient and secure network.
Architectural Approaches for Modern Network Defense
Knowing the threats is one thing; building a network that can actively shut them down is another entirely. For years, network security followed a simple "castle-and-moat" model: build a strong wall around the perimeter and assume everything inside is safe. In today's world of sophisticated attacks that can start from both inside and outside, that idea is dangerously outdated.
Modern defence is all about smarter, more dynamic strategies. These aren't just tools you buy, but blueprints for creating a network that’s both resilient and intelligent. Instead of one big wall, we’re building a series of internal defences, questioning every connection, and using the latest standards to bake security in from the very start.
Building Digital Walls with Network Segmentation
A core strategy in any modern network is Network Segmentation. Think of your business as a large building with different departments. You wouldn't give the receptionist a key to the server room, would you? Segmentation applies that same common-sense logic to your network, creating isolated zones for different users and devices.
This is done by carving up a larger network into smaller, self-contained sub-networks. Each of these segments gets its own set of access rules, effectively building digital walls between them. For a hotel, this is non-negotiable: the guest WiFi network must be completely separate from the one running payment terminals or staff systems.
Why is this so vital? It contains the blast radius of an attack. If a device on the guest network gets compromised, segmentation stops the attacker from moving laterally to raid critical corporate data. The breach is firewalled within its own small zone, dramatically reducing the potential damage.
Zero Trust is a strategic mindset, not a single product. It's a fundamental shift away from the old model of "trust, but verify." The new rule is simple: "never trust, always verify." Every single access request, every time, has to be authenticated and authorised.
Embracing the Zero Trust Model
Building on the idea of segmentation, the Zero Trust security model takes this principle to its logical conclusion. It works from one powerful assumption: threats can exist anywhere—outside and inside your network. Because of this, no user or device gets a free pass, no matter where they are connecting from.
Every single attempt to access a resource must be strictly verified. Picture it like a high-security facility where you have to show valid credentials at every single door, every single time, even if you’re already inside. This constant verification process means that even if an attacker manages to compromise one account or device, their ability to move around is severely restricted. They can't just wander over to the next server because every step requires a fresh authentication they simply don't have.
This map highlights some of the key network threats that these modern architectural approaches are designed to defeat.
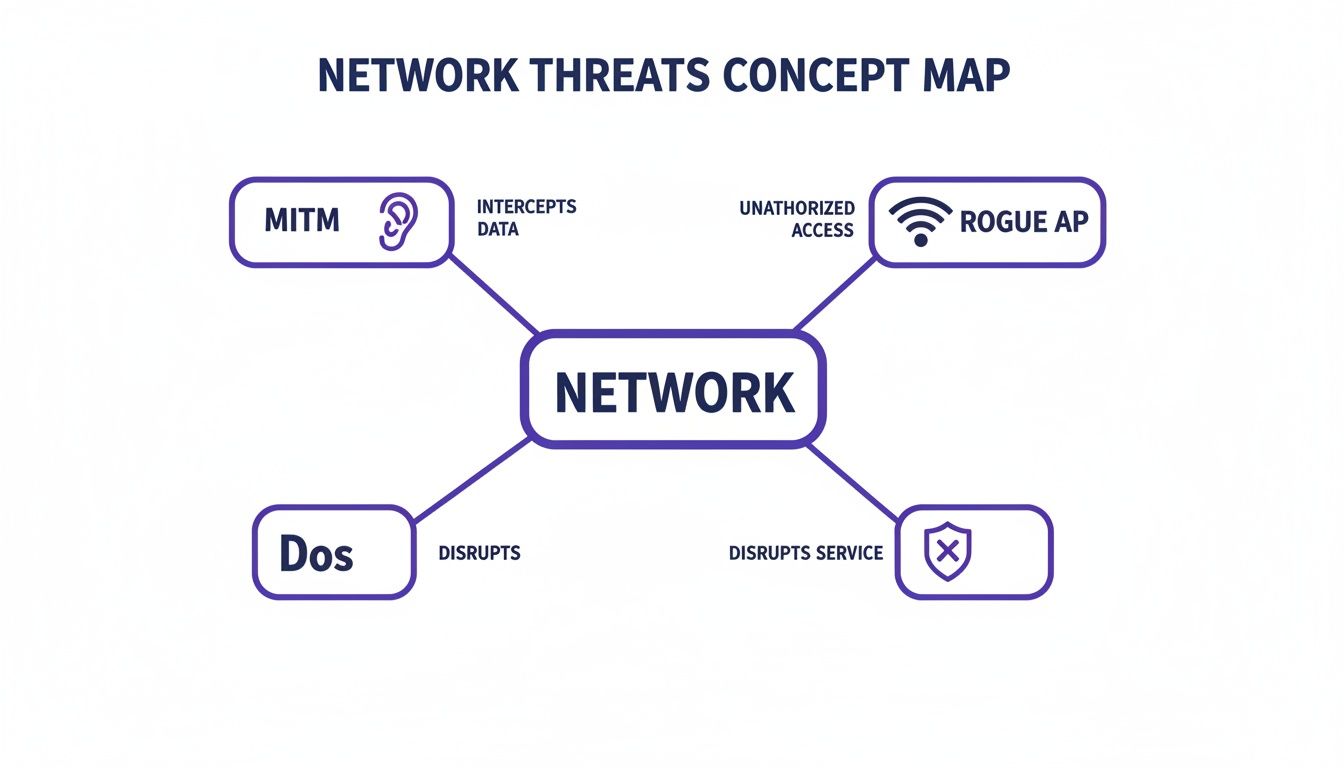
It shows how threats like Man-in-the-Middle attacks, Rogue Access Points, and Denial-of-Service directly compromise a network's integrity and availability, reinforcing why we need a proactive defence-in-depth strategy.
Upgrading Wireless Security with WPA3 and OpenRoaming
For any business that offers WiFi, the specific security standards you use are paramount. Older protocols like WPA2 have been workhorses for years, but they have well-known vulnerabilities that attackers are actively exploiting. The latest standard, WPA3, delivers a massive security upgrade.
WPA3 strengthens encryption, making it much harder to crack, and protects against common offline "dictionary" attacks where hackers try to guess passwords. Critically, it also ensures that on open, public networks, each user's traffic is individually encrypted. This stops someone sitting at the next table from snooping on their activity.
This concept of seamless, secure connections is perfected by technologies like Passpoint and initiatives like OpenRoaming. They automate the entire connection process, using a person's existing identity (like their mobile carrier or company login) to get them online securely without them having to do a thing.
This delivers a triple-win for network security:
- Eliminates Rogue AP Risk: Users aren't picking a network name from a list, so they can’t be tricked into connecting to a malicious "Evil Twin" hotspot.
- Encrypted from the Start: The connection is secure from the very first packet, closing a major vulnerability found in traditional open networks.
- Frictionless Experience: It gets rid of clunky login pages and shared passwords, which are not just a security nightmare but also a terrible user experience.
By combining segmentation, a Zero Trust philosophy, and modern wireless standards, any organisation can build a multi-layered defence that is far more effective at stopping today's threats. It creates a network that isn't just secure by design, but also intelligent and ready for the demands of modern business.
Implementing Identity-Based Access for Ultimate Security

Real network security starts by flipping an old question on its head. For decades, IT admins have asked, "What is this device allowed to do?" But the modern, Zero Trust way of thinking poses a much smarter question: "Who is this user, and what are they authorised to access?"
This simple shift is the foundation of identity-based access control. It’s a move away from the shared passwords and pre-shared keys (PSKs) that have been a security weak point for years. A shared password is like leaving one key under the doormat for the entire office—once it's found, you have no security at all. Identity-based access tosses that model out the window.
Instead, every single user and device gets its own unique, unforgeable digital passport. This isn't just a password; it's a verifiable identity that proves who they are and grants them precise, limited access based on their role.
Automating Staff Access with Identity Providers
For your employees, bringing this modern approach to security in networking is surprisingly straightforward, thanks to integrations with established identity providers (IdPs). These are likely services your organisation already relies on every day.
- Microsoft Entra ID (formerly Azure AD)
- Google Workspace
- Okta
When you connect a network access platform to these directories, the whole process of securing staff connections becomes almost automatic. There's no more manual account creation or handing out shared WiFi passwords. The system simply issues unique digital certificates to each employee's devices.
This certificate acts as their secure passport. When an employee is near the office network, their device presents this credential, gets instantly verified against the directory, and is granted access. No passwords to remember, type, or have stolen. And if someone leaves the company? Revoking their access is as easy as updating their status in the IdP, which instantly voids their digital passport.
To get a better handle on how this works, you can explore our in-depth guide to identity-based WiFi security.
Securing Guest Access Without Passwords
This identity-first mindset isn’t just for staff. For guests in a hotel, shop, or venue, asking them to juggle passwords is both insecure and a terrible experience. Let’s face it: people’s security habits are often poor, creating a huge risk when they connect to business networks.
A recent survey found that a staggering 47% of UK broadband households have never changed their default router settings. Even worse, 69% admitted they had never changed their WiFi password. These habits don't magically improve when people are away from home, highlighting why systems that don’t depend on user-managed passwords are so critical.
This is where technologies like OpenRoaming completely change the game for guest access. It delivers a similar password-free, identity-based connection for the public.
OpenRoaming uses a visitor's existing trusted identity—such as their mobile phone provider or a social login—to automatically and securely connect them to the WiFi network. The entire process is seamless, encrypted from the very first packet, and completely removes the user from the security equation.
By authenticating the user via a trusted third party, your network can grant secure access without ever needing a shared password or a clunky captive portal. It proves that ironclad security and a completely frictionless user journey can absolutely go hand in hand. This is the future of public network access—secure, simple, and built around identity.
Practical Deployment and Monitoring Strategies
Turning security theory into a real-world defence that actually works takes a clear, actionable plan. A strong security posture isn’t something you achieve by just installing a new product; it’s built through thoughtful deployment and maintained with diligent, ongoing monitoring. This is where the architectural blueprints we've talked about become a tangible reality on your network.
The first step is a strategic rollout that closes security gaps quickly and efficiently. This all comes down to careful planning around a few key operational pillars.
Planning Your Deployment
An effective deployment always starts with mapping out your existing environment. It’s crucial to integrate new security solutions with the infrastructure you already have, not fight against it. Modern platforms are built for this, designed for compatibility with leading hardware vendors like Meraki, Aruba, and UniFi to ensure a much smoother rollout.
A few key things to sort out from the start:
- Network Segmentation Plan: Figure out exactly how you'll isolate different types of traffic. You need to define clear boundaries between your guest WiFi, staff access, point-of-sale systems, and critical backend servers.
- Identity Directory Integration: Link your access control platform to your existing identity providers, like Entra ID or Google Workspace. This automates the whole process of giving and revoking access for staff as they join or leave.
- Hardware Compatibility Check: Double-check that your chosen solution plays nicely with your current switches, access points, and firewalls. This helps you avoid any nasty surprises or compatibility headaches during setup.
Solid network management is the bedrock of good security. Knowing the fundamentals, like the procedures for resetting Cisco switches, is essential for maintaining network integrity when things go wrong.
Continuous Monitoring and Incident Response
Once your secure network is up and running, the job shifts from implementation to vigilance. Network security is never a "set it and forget it" task. Continuous monitoring is all about keeping a watchful eye on your network for signs of trouble and having a clear plan to act the moment you spot something.
This process turns security from a theoretical exercise into a living, proactive posture. It involves collecting and analysing network data to spot anomalies that could be the first whisper of an attack.
Monitoring without a plan is just collecting data. A formal Incident Response Plan turns that data into decisive action, outlining the exact steps your team will take from the moment a threat is detected to its final resolution.
An effective monitoring strategy requires watching for specific red flags. These indicators are often the earliest signs of a security breach, giving you a chance to respond before real damage occurs. Proactive DNS filtering, for instance, is an incredibly powerful layer of defence here. You can learn more about how this works in our guide explaining why proactive DNS filtering is your best defense against modern threats.
Your team should be actively looking for:
- Unusual Traffic Patterns: A sudden, unexplained spike in data flowing to or from a specific device or external location can be a tell-tale sign of a data breach or malware activity.
- Spikes in Failed Logins: A high volume of failed authentication attempts against a single account or system often means a brute-force attack is in progress.
- Connections to Suspicious Destinations: Outbound traffic to known malicious IP addresses or domains is a strong indicator that a device on your network has been compromised.
- Unauthorised Device Detections: Any new, unknown device popping up on a secure network segment demands immediate investigation. No exceptions.
By combining a well-planned deployment with a disciplined monitoring and response strategy, you create a living security framework—one that can adapt and react to whatever the constantly changing threat landscape throws at it.
Turning Your Secure Network into a Business Asset
Thinking of top-tier network security as just another expense is an easy mistake to make. We often see it as a defensive cost—a necessary evil to prevent disaster. But that view misses a massive opportunity. When you build your network the right way, particularly with an identity-based platform, it stops being a cost centre and starts becoming a strategic asset that actually fuels growth.
The magic is in the first-party data you gather during the secure sign-in process. Every single time a customer or guest connects to your WiFi, you create a direct, consent-based relationship with them. This is so much more than just handing out an internet connection; it's the beginning of a conversation.
From Cost Centre to Growth Engine
This is where things get really interesting. When you link that rich identity and behavioural data to your Customer Relationship Management (CRM) and marketing platforms, you can start to personalise the customer journey in ways that simply weren't possible before. For businesses in hospitality, retail, and large venues, this is a game-changer.
- Personalised Offers: A hotel can greet a returning guest with a welcome message and an offer for their favourite drink at the bar, right as they check in.
- Deeper Insights: A retail centre can analyse footfall patterns to see which entrances and shops are busiest at different times, helping them optimise everything from store layout to staffing rotas.
- Increased Loyalty: A café can automatically add loyalty points to a customer's account every time they log into the WiFi, giving them a compelling reason to come back.
An investment in a modern, identity-based networking platform isn't just a security measure. It's a strategic business decision that delivers a clear return in a world full of threats and fierce competition.
Proving the Return on Investment
This approach shifts network security from a line item on the expense sheet to a measurable contributor to your bottom line. It's not just theory; the numbers back it up. The UK's cybersecurity sector, for instance, generated £13.2 billion in gross value added, with major growth on the horizon as more businesses react to widespread breaches. You can discover more about the UK's cyber security sector analysis to see the full scale of the market. This isn't just about IT; it's a core business function.
Here’s a real-world example: a large shopping centre used its WiFi analytics to discover that visitors who connected to the network stayed 20% longer and spent more money per visit. That's a powerful insight. By using that data to run targeted promotions, they directly boosted their revenue. It's proof that the right investment in security in networking pays for itself many times over, building a smarter, more profitable business long after the initial setup is complete.
Your Network Security Questions, Answered
As you start tightening up your network security, some practical questions are bound to pop up. Here are some of the most common things we hear from IT admins and managers as they get started, reinforcing some of the core ideas we've covered.
What’s the First Step to Improving Our Guest WiFi Security?
Get rid of open, password-free networks and insecure shared passwords. Seriously. The most critical first step you can take is moving to an identity-based system. This single change closes some of the biggest security gaps right away.
It immediately transforms your network from an anonymous free-for-all into an environment where every connection is tied to a unique identifier. This lays the groundwork for every other modern security measure, from monitoring and control to proper network segmentation. You're essentially starting a secure digital relationship with your users from their very first connection.
The goal is to eliminate anonymity. Whether it’s through a secure portal that captures an email or a seamless technology like OpenRoaming, tying every connection to a verifiable identity is the single most impactful change you can make.
How Does Zero Trust Work in a Real-World WiFi Environment?
In a WiFi setting, Zero Trust is simple: trust no one and nothing by default, no matter where they are on your network. Every single connection request has to be verified, every single time. It creates a much tougher environment for anyone trying to gain unauthorised access.
For your staff, this might mean using an identity provider (like Entra ID) to issue unique certificates to each device, granting them access only to the specific resources they absolutely need to do their job. For guests, systems like OpenRoaming encrypt the connection from the get-go, while network segmentation keeps them completely walled off from your corporate resources.
Is Switching to a Secure Identity-Based Platform Difficult?
It's more straightforward than you might think. Modern cloud-based platforms are built for rapid deployment and are designed to integrate smoothly with the network hardware you already have from major players like Cisco Meraki, Aruba, and Ruckus.
The process usually involves configuring the platform to sync with your current WiFi infrastructure and identity providers. What used to be a complicated, months-long project can now be up and running in a matter of weeks. This gives you a fast track to enterprise-grade security without the headaches of old-school on-premise solutions, making robust security a realistic goal for organisations of any size.
Ready to replace outdated shared passwords with a secure, identity-based networking platform? Learn how Purple delivers Zero Trust security with a frictionless user experience. Explore the Purple platform.











